The number of mobile . subscriptions in the world is now as large as the number of people. To ensure future market growth, the mobile industry is working towards a vision that will make today’s use of mobile communications look like a mere starter.
Introduction
By the use of a massive technology step in wireless communications, the successor to 3G and 4G mobile technology—5G—will open the way for the Networked Society, in which wireless technology will be used to connect equipment within all sectors of society. Sweden is one of the leaders in the development of 5G and this shift in paradigm may unleash tremendous opportunities for economic growth.
At the same time, several highly important strategic choices will have to be made, both by the responsible authorities and business actors, to deal with society’s increased vulnerability and citizens’ privacy issues. This massive increase in wireless systems will increase the vulnerability to attacks using electromagnetic interference and cyberattacks, since such attacks can be performed at a distance from a wireless system. In recent years, researchers have demonstrated some of the possibilities; several examples are highlighted in more detail below.
Driving Forces Behind The Vision
Every ten years or so, technology steps occur in mobile communications. Once a decade, a new generation of mobile network technology comes along: the first mobile networks (1G) appeared in the 1980s, GSM (2G) followed in the 1990s, 3G arrived at the turn of the century, and LTE (Long Term Evolution) began rolling out in 2010, and has evolved to 4G. Sweden has always been one of the leading countries in the industrial development of all these generations, and remains so now. This time, however, the ambition level is dramatically higher and a tremendous technology step is planned.
The main cause of the mobile industry’s high ambition level for 5G is to be found in economic considerations. Mobile data usage is rapidly increasing in both handheld devices and laptops. It is estimated that global mobile data traffic will grow by more than 200 times from 2010 to 2020, and by nearly 20,000 times from 2010 to 2030. Therefore, new investments and upgrades are necessary to meet and keep up with the demand for higher data transfer rates in mobile broadband networks. The operators are facing a number of challenges related to the scalability and cost structure of cellular systems, all of which must be resolved if ever higher data rates are to be ensured.
At the same time, the use of flat-rate subscriptions (a fixed price per month for mobile broadband) limits revenues, since the user cost for a mobile subscription has been reduced or remained constant in recent years. This has created a situation known as the ”revenue gap,” shown schematically in Figure 1.
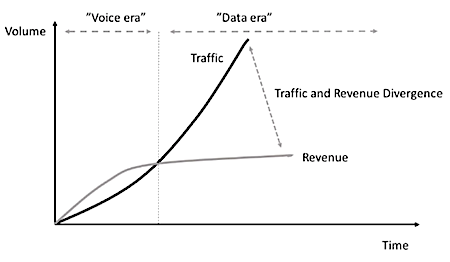
A new concept of cost-efficient scalable infrastructure for the growing amount of mobile data must be found. Furthermore, since the number of mobile subscriptions that are possible in the world is finite, given the limited number of people, new applications for mobile broadband communications are necessary to ensure further market growth. The answer is to equip most electronic devices with wireless Internet access. By doing this within most sectors of society, we will create the Networked Society. 5G is expected to be the first network designed to be scalable, versatile, and energy-smart for a hyper-connected “Internet of everything.”
The idea of connecting devices that are not handled by persons is not new in itself. The potential “Internet of Things” (IoT) has been discussed for several years. However, such connections to the Internet are still very much isolated initiatives, and IoT applications are typically developed as specialized solutions. The consequence is limited connectivity between the products offered by different vendors or for different domains, e.g. for transport, energy, or “smart cities.”
The 5G vision can be seen as the necessary technical enabler to really make IoT happen at full scale. 5G is being designed as the key enabler of the future digital world, where ubiquitous ultra-high broadband infrastructure will support the transformation of processes in all economic sectors and meet the growing consumer market demand. The wireless part of global Internet traffic is expected to grow from approximately 50% today, to about 75% in 2020, and the first 5G products are expected to be available in 2020.
As Sweden is one of the top leaders in telecommunications, we have always been early adopters of new telecommunication services in different social applications. This means that Sweden will be one of the first countries to experience the new challenges that this massive adoption of wireless technology will create for society. It is the kind of situation that presents both opportunities and challenges. By making the right choices, Sweden may be able to take advantage of the former rather than struggle with the latter.
The 5G Vision
The vision of the Networked Society involves, in principle, all sectors of society, as seen in Figure 2.
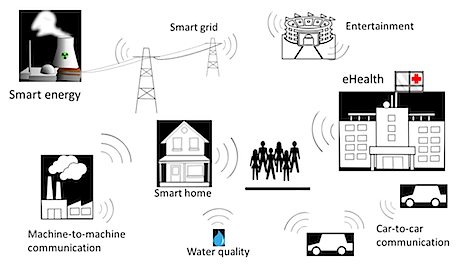
Examples of 5G applications are ubiquitous: smart cities, e-health, smart homes, smart grids, smart agriculture, intelligent transport systems (ITS), logistics, industrial control, environmental monitoring, education, entertainment and media. The potential is considered so far-reaching that some actors are already saying that a new gold rush is being spurred by the opportunities of the Networked Society. The technical goals for 5G are so ambitious that today’s performance will be massively exceeded.
Examples are a 10-100 times higher user data rate, 1000 times more mobile data per area (per user), 10-100 times more connected devices, and 10 times longer battery life for low-power massive machine communications, where machines such as sensors or pagers will have a battery life of a decade. It is expected that these requirements will be fulfilled at a similar level of cost and energy dissipation per area as in today’s cellular systems. Thus, the 5G vision is not just a traditional step in evolution from previous generation mobile systems; it is a true shift of paradigm. In the Networked Society, the flow of information between devices will be dramatically increased.
Yet with new technology steps, there are always new challenges to grapple with, and technical availability alone is not the sole criteria for bringing a specific technology into use. In the present case, the vulnerability of both the societal and individual privacy aspects need to be handled in an appropriate way. This immediately raises several questions about security and privacy and calls for important strategic choices to be made.
Vulnerabilities that demand strategic choices
Wireless technology itself creates new vulnerability compared with wired connections. Deliberate attacks on wireless systems require no access to the direct physical location of the system, but can be performed at a distance. Thus, cyberattacks that until now have only been possible when carried out within wired networks can be performed at a convenient physical distance from the wireless systems. Since all wireless devices are designed to receive limited signal levels in the air, they can be blocked simply by transmitting a stronger signal in the appropriate frequency band. Standard civilian wireless technology is in general not robust against such interference signals, and better protection against them is in general expensive.
Wireless systems can be attacked in several ways, for example by jamming, with the aim of disrupting transmission and thus creating a Denial of Service (DoS); eavesdropping, for acquiring critical information from the transmission; and spoofing, to enable manipulation of the system with false information. It is crucial to reflect on these threats in advance, so that society-critical services will not be dependent on wireless solutions that are easily vulnerable to attack. Criminal actors are already exploiting that vulnerability: Swedish and international media regularly report, for instance, how jamming is being used in connection with theft and burglary.
An example of how an everyday device equipped with wireless access can increase vulnerability to cyberattack was provided by former US Vice President Dick Cheney, when he was interviewed on CBS’s 60 Minutes programme, on 20 October 2013. Mr Cheney said that he was so concerned that terrorists might hack the medical device implanted near his heart that he had disabled its wireless access. The computer security expert, Barnaby Jack, later demonstrated, at the BreakPoint Security Conference in Melbourne, how he could remotely and suddenly cause a pacemaker to deliver an 830 volt shock.
In 2015, two security researchers, Charlie Miller and Chris Valasek, demonstrated that they could hijack a vehicle over the Internet, without any dealership-installed device to facilitate access. By hacking into a 2014 Jeep Cherokee, the researchers were able to turn the steering wheel, briefly disable the brakes and shut down the engine. Later, Fiat Chrysler Automobiles issued a voluntary safety recall to update the software in about 1.4 million U.S. vehicles.
Another example is the demonstration, by security researchers, Runa Sandvik and Michael Auger, of how a remotely-controlled smart rifle from TrackingPoint could be hacked from a distance. Their technique can wreak havoc with the gun’s targeting computer, causing it to miss its target or prevent the rifle from firing. In a real situation, such intervention would mean that the operator would have lost control over the weapon.
Although the above are only a few examples of what is already possible today, they indicate how a rapid and massive increase of wireless Internet access is creating a completely new and evolving complex of security threats. The European Cybercrime Centre, EC3 (Europol), foresees more targeted attacks on existing and emerging infrastructures. These include new forms of data theft, blackmailing and extortion schemes, such as ransomware.
Ransomware is a type of malware that allows its creator to infect a system (e.g., a smart car, or smart home) and restrict access to it until a ransom is paid. Not only financial harm, but even physical injury and possibly even death are among the potential outcomes of such penetration.
Trust will be, and needs to be, the basic foundation of the Networked Society and it must be underpinned by security and privacy. If not, the vulnerability of critical services will rapidly increase, at the same time as the industry will be unable to exploit the full business potential. Just one of many important strategic choices is the need to decide: in the Networked Society, what society-critical functions should be connected to the Internet in the first place?
Allowing surveillance systems, first-responder systems, border-control systems, energy systems, air traffic control or water systems to become part of the Networked Society will open up for increased vulnerability to deliberate attacks. An important strategic decision would be to choose selected parts of critical infrastructure for complete exclusion from being connected to the Internet at all.
A similar issue concerns which society-critical functions should be wirelessly connected to the Internet, since, as explained above, this makes possible both hacker intrusions and jamming attacks at a distance from the system. Here, one choice could be to allow wireless access to critical systems only within a controlled physical area, where only authorized personnel have access.
The vision for the Networked Society is to make our everyday lives easier and boost the efficiency and productivity of businesses and their employees. The data collected will help us make smarter decisions. But this will also have an impact on privacy expectations. If data collected by connected devices is compromised, it will undermine trust. Data about energy consumption in a house, the technical status of various household appliances, and so on, may be used not only by business actors, but by criminals who might want to check whether the house is empty. And how do we handle the ethical aspects of how to use data from health monitoring, sent from a wireless bracelet?
It must be made clear to the average consumer how the use of data is regulated with respect to privacy and ethical concerns. Without such clarity, it might be difficult to make the average consumer an enthusiastic user of all services in the Networked Society. This applies especially to Europe, where previous research in IoT projects indicates that concern about privacy is very important. Since Sweden is one of the leading countries working with this vision, it is reasonable to assume that this shift of paradigm will reach our society at an early stage. Again, this may provide us with a greater opportunity not only to protect our own society from threats, but to strengthen and profit from our lead in the know-how and technology that goes with being a world leader in the field.
The Internet is still not secure, so we cannot expect the Networked Society to be secure either. However, security is constantly evolving to meet new challenges, and awareness of Internet security is strong among the responsible authorities in Sweden. A recent example is the report, Information Security—Trends 2015, a Swedish Perspective (report MSB851), jointly produced by The Swedish Armed Forces, the National Defence Radio Establishment, the Swedish Civil Contingencies Agency (MSB) and the Swedish National Bureau of Investigation.
The report addresses seven trend areas and gives an overall picture of the situation in the information security field, as it stands now; the coming massive increase of wireless systems in the Networked Society, however, will further increase its complexity and the vulnerability. Therefore we are bound to meet ever newer challenges, both regarding Internet security and electromagnetic interference, as discussed above.
To maximize the opportunities and minimize the vulnerabilities of the Networked Society, it is more important than ever that thoughtful strategic choices are made long in advance, since the complexity of the coming technology step might not leave room for ad hoc solutions afterwards. Questions about the extent to which society-critical services should be part of the Networked Society, and how the massive amounts of information available in these networks should be handled, must be decided in advance, if we want to avoid creating a highly vulnerable society with low trust from its users.
The vision of the Networked Society offers the largest opportunities, in civilizational terms, but also the most complex challenges with respect to security and privacy, of any previous technology step taken by our society.
Peter Stenumgaard
This is a reprint of the article in the report ”Strategic Outlook 6”, issued by the Swedish Defence Research Angency (FOI). The full report can be downloaded here.
Peter Stenumgaard has a PhD in radio communications. He is a Research Director and works as Head of the Department of Information Security & IT Architecture at FOI. He has worked as adjunct professor, both at Linköping University and the University of Gävle. He has long experience of research in both military and civilian applications and has also been the director of the graduate school, Forum Securitatis (funded by Vinnova), within Security and Crisis Management. He worked for several years on the JAS fighter aircraft project, on the protection of aircraft systems against electromagnetic interference, lightning, nuclear weapon-generated electromagnetic pulse (EMP) and HPM (high-power microwaves).


